All you need to know about multi-cloud security
By Alex Hawkes|20 June, 2022

A recent study from Juniper Research predicts the value of enterprise cybersecurity spend will continue to climb, exceeding $226 billion in 2027; up from $179 billion in 2022. This growth of 26% over the next five years reflects a rising awareness of vulnerabilities, not least of which is DDoS (Distributed Denial of Service) as a key driver behind the increasing spend.
When it comes to things that keep network engineers and IT teams awake at night, security is a common concern. With a large number of employees now working remotely and businesses of all sizes relying on multiple public clouds and SaaS (Software-as-a-Service) apps, network perimeters aren’t as clear as they once were.
The delivery of mission critical applications from the public cloud also means many risks are now outside the control, and even off the radar, of network engineers and IT departments. While cloud-based apps have enabled businesses to adopt new ways of working almost overnight, this shift in the way enterprises work has brought with it new network security headaches due to changes in both user and attacker behaviour.
As identified by Juniper Research, with so much of today’s business relying on digital infrastructure, Denial of Service (Dos/DDoS) attacks have become commonplace and relatively easy for attackers to pull off, with the intention of severely disrupting corporate networks.
On the face of it, a multi-cloud approach has a natural level of redundancy, which is one way of dealing with this particular challenge, but the potential downside means you are spreading potential threats across multiple parties.
Misconfiguration in a multi-cloud world
As we have discussed in previous articles, there is no real incentive for the multitude of cloud providers, from AWS, to Microsoft Azure, to Google Cloud Platform, IBM Cloud and Oracle Cloud, to standardise on their own infrastructure. This means several different environments with several different workflows.
As with most security threats, the most common culprit is misconfiguration and when it comes to the cloud, the type of misconfigurations we see most often are similar to those we see in a data centre environment. Typically it’s not a ‘cloud’ misconfiguration as such but one or more of the services or software applications running within the environment.
The culprit is primarily a lack of experience in configuring one or more cloud infrastructures. Because the cloud has made it easier to roll out new apps and services, we typically have lots of new users of IT services that are not as security conscious as IT specialists.
As API usage has become more prevalent, one of the benefits of rich APIs that has emerged is that infrastructure components are able to talk to each other in unprecedented ways, making it easier to cover the entire surface area of a cloud instance from a security perspective.
Security visibility in a multi-cloud world
Relying on third party cloud-based platforms and services also brings other challenges. As discussed, each cloud environment comes with its own specific tools and support systems, such as libraries, APIs, operating systems, and architecture. So, electing to build an app in one environment may therefore deliver a certain amount of vendor lock-in, and switching platforms down the line may mean rebuilding the application for another environment.
But the ease-of-use of public cloud platforms means everything is done and stored on the platform, which can reduce granular visibility into where and how data is stored by the provider. This can obfuscate the security and compliance protocols employed by the provider.
Maintenance in a multi-cloud world
Just as we’re seeing personal and professional lives blend from living and working in the same location, working hours have also changed dramatically. Many businesses have adopted a more flexible approach to working and the removal of the commute means different start or end times for some, with other employees working more frequently on evenings and weekends. All of this has an impact on the network traffic, which historically has been more predictable.
“The work day is kind of getting spread out a little like peanut butter. We're not seeing those significant lows during the day that would traditionally be evening hours,” said Jay Turner, vice-president, development and operations at Console Connect by PCCW Global.
This is problematic when it comes to network maintenance and rolling out critical or regular security fixes, because it has been much harder to conduct without the predictable periods of downtime that used to be a part of everyday business.
Network redundancy has always been essential when carrying out any infrastructure maintenance to ensure there is no period of service disruption for workers, meaning businesses now have to think about ways of introducing redundancy outside of the traditional patterns.
Bolstering multi-cloud security with Network-as-a-Service (NaaS)
Because the cloud has made such a diverse array of tools and services available, adequate connectivity has become a stumbling block, especially in hybrid and multi-cloud environments.
Poor connectivity can easily degrade application performance, even if it is only connectivity to a specific part of the application infrastructure. A snappy front end can be let down by an app that relies on an unstable data centre interconnect to query a database on the backend. While a lack of redundant networking means employees are disrupted by routine maintenance.
Furthermore, when securing traffic in transit, encryption can help protect sensitive data, but encryption can also make it harder to monitor that traffic and network activity and it adds capacity and processing overheads into the mix that can eat into bandwidth and connectivity capability.
But Network-as-a-Service (NaaS) offers a flexible solution for many of these challenges. It’s on demand, pay-as-you-use model makes it highly versatile in highly unpredictable situations, enabling network managers to fire up connections when you need additional bandwidth, for network maintenance or application updates for example, and tear the circuit down when done.
For spikes in activity you can dynamically scale the network bandwidth in order to accommodate, while establishing dedicated private connections to your cloud provider can also help alleviate some of the demands on your corporate network caused by remote working. Dedicated or direct interconnect provides a physical connection between assets, maximising the security and performance of the network while increasing cost.
Using Console Connect, businesses can directly connect to major cloud platforms, including Amazon Web Services, Microsoft Azure, Google Cloud, and IBM Cloud, as well as the entire ecosystem of SaaS providers, boosting security and reliability.
NaaS also gives you a connectivity mechanism between data centres and between private and public clouds, like your own personal ethernet cable strung between a data centre in London and a data centre in New York, with all the additional benefits of improved security, monitoring, and management options.
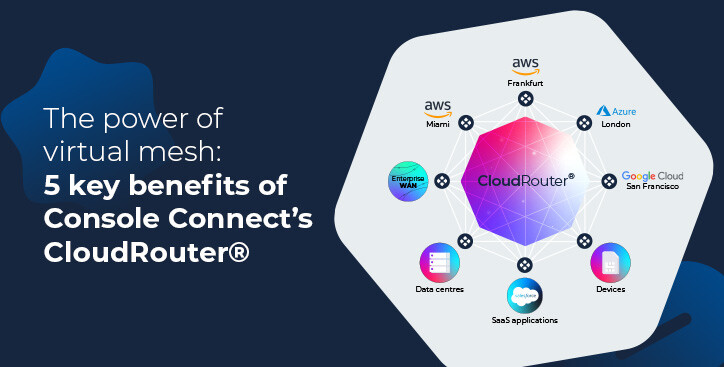
But whereas existing Layer 2 direct connections enabled by a NaaS such as Console Connect require a physical cross connect or some way of meeting the MPLS network at a Point-of-Presence, a new Layer 3 technology, CloudRouter by Console Connect, enables organisations to build a virtual network overlay to meet their multi-cloud needs in a matter of minutes, without the expense of additional racks and routers.
Just as NaaS takes the headache out of managing a complex Layer 2 environment by making it very easy to set up and manage your network from one portal, CloudRouter extends this capability to the IP layer, enabling you to provision a mesh network connecting multiple clouds together in a matter of minutes.